If you had a chance to read the first article in my cybersecurity series, you learned a little about phishing schemes. Phishing is the easiest and least sophisticated form of what cybersecurity experts refer to as social engineering. Cybersecurity firm Kaspersky calls social engineering “manipulation” and “human hacking.” What does that mean?
The phishing techniques in the previous article were clearly aimed to trick people. However, there was not enough interaction between the crook and the potential victim to suggest that individuals were hacked or manipulated by the attacker. Phishing is a numbers game.
More sophisticated social engineering involves research and targeting of specific people or groups (sometimes called “spear-phishing”), and often involves direct communication between crook and target. The goal of the attacker remains the same in either case. They would like you to engage, divulge sensitive information, and / or send money under false pretenses. Many people think of social engineering in terms of email (or maybe social media). However, these scammers may call people, or even interact with someone in person. For the sake of this article, we will focus on digital (originating online) social engineering threats.
Real life examples of sophisticated social engineering schemes:
Impersonation (when using email, this is called spoofing):
Obviously an internet scammer is not going to come out and tell you his or her real name. Generally, these scammers impersonate someone you know. Often, they choose someone you are eager to help like your coworker or boss. These crooks have done some background research on their target and the person they are impersonating. Below is an example of such a scheme. In this instance, the scammer targeted Sensible’s Human Resources professional, Anne Smith, while impersonating Rick Miller (Sensible’s CEO). The hacker used an email “spoof” so that the message to Anne appeared to be coming from Rick’s email.
Anne and Sensible Financial were able to determine this was a social engineering scheme and Rick continues to get his paycheck in the right place.
Hacked email:
In the example above, Rick Miller’s email address was spoofed (see tip below on how to spot these). However, scammers may gain control of someone’s legitimate email address, and scams generated from a known and familiar email address can be tougher to spot. In this example, a client’s email address was hacked. The hacker sent Sensible a request for money from the client’s actual email address and using a specific bank and beneficiary (all redacted or edited for privacy).
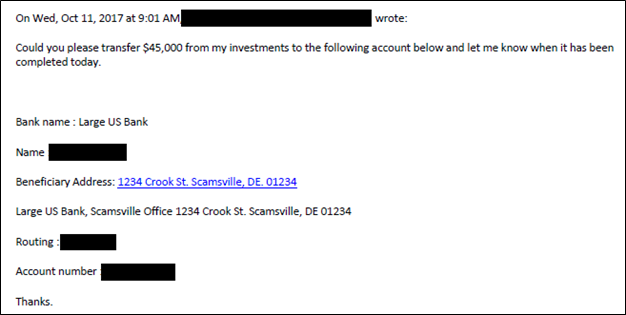
Sensible spotted this email as fraud. However, we were concerned because it came from our client’s email address. The advisor immediately called the client to inform them their email had been hacked.
Romance swindles and pig-butchering
I know this one sounds awful. While Sensible thwarts social engineering scams where someone is trying to divert funds from a client (or employee), we don’t see a lot of romance scams or schemes known as pig-butchering. These scams usually target individuals and may start from a text message or social media message rather than an email.
Romance scams are exactly what they sound like. The scammer entices the victim with a friendly and interested dialogue and then exploits the trust and affection of the victim.
Like phishing, pig-butchering (named after the practice of fattening a pig before slaughtering) may be random and not specifically targeted to one person or a group. However, like romance scams, once they have their mark, they take advantage of someone’s friendly and trusting nature. In this attack, the scammer will send a message (usually a text or social media message) that appears to be sent to the wrong person. When the victim replies to inform them they have the wrong number, the scammer strikes up a dialogue. The conversation is usually around fake crypto currency or another phony investment that promises great returns. Eventually, the victim sends money to the scammer, and then the scammer disappears.
How do we (Sensible) protect ourselves and our clients from social engineering attacks?
Policies and procedures / technology:
In both Sensible Financial examples above, we caught these scams before they took root. However, if the crooks were able to convince an employee to try to send money to a new (third-party) account, we and our custodians have procedures (supported by technology) in place that make this very difficult to pull off. If you are a Sensible Financial client and have recently sent a third-party wire, you know what we are talking about.
Culture and training:
Since social engineering involves the manipulation of people, culture and training are extremely important. Sensible has a culture of cyber security awareness, and as a group we regularly discuss our experiences or new information we’ve learned. We also train our employees on how to catch scams.
How can you protect yourself from social engineering scams?
Scrutinize, scrutinize, scrutinize:
Never respond to, or engage with, communications from people or organizations you aren’t familiar with. If you are contacted by a person or an organization you are familiar with, but they are asking for sensitive information, hang up (or delete the email) and call the person or company back on a number you know is real (from their website or your phone contacts).
Learn to spot a “spoofed” email address:
If you get an odd email and the sender’s name is familiar, this could be a spoofed email. If you hover the cursor over the email address or (on your phone) expand the “from” field in the email, it will show you the sender’s actual email address. My screenshot below shows that the email was spoofed as Frank Napolitano but it really came from this wacky Gmail address and not from Frank.

The content or subject of the message / tone / writing style / grammar:
So, your cousin Mike emails (or Facebook Messages) you out of the blue and asks for $5,000. You’ve confirmed it’s really Mike’s email address (or Facebook account) but that doesn’t sound like Mike. He also spelled your name wrong and is using strange words Mike would never use. Mike has likely been hacked and the scammer is reaching out to his contacts in the hopes someone is willing to send Mike $5,000.
Keep learning:
The disclosure at the bottom of this article will let you know I am not an expert in cybersecurity. However, I’ve learned a lot from my own experiences (personal and professional), talking to experts, and reading a lot about what threats are out there, and how to stay protected. The Center for Internet Security has a pretty good monthly newsletter that isn’t overwhelmingly “techy”. Check out some of their previous newsletters and if you like them, you can sign up to receive them in your email.
*FULL DISCLOSURE: Chuck Luce and Sensible Financial are not cybersecurity experts. This article is not intended to fully educate readers on all aspects of social engineering, cyber threat protection, or cybersecurity. Please talk to your advisor if you have any questions or concerns about keeping your assets and digital information safe and we can point you to some helpful resources. Here is a great place to start.